CVE-2023-4966
Citrix NetScaler ADC and NetScaler Gateway Buffer Overflow Vulnerability - [Actively Exploited]
Description
Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server.
INFO
Published Date :
Oct. 10, 2023, 2:15 p.m.
Last Modified :
Oct. 24, 2025, 1:42 p.m.
Remotely Exploit :
Yes !
Source :
[email protected]
CISA KEV (Known Exploited Vulnerabilities)
For the benefit of the cybersecurity community and network defenders—and to help every organization better manage vulnerabilities and keep pace with threat activity—CISA maintains the authoritative source of vulnerabilities that have been exploited in the wild.
Citrix NetScaler ADC and NetScaler Gateway contain a buffer overflow vulnerability that allows for sensitive information disclosure when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server.
Apply mitigations and kill all active and persistent sessions per vendor instructions [https://www.netscaler.com/blog/news/cve-2023-4966-critical-security-update-now-available-for-netscaler-adc-and-netscaler-gateway/] OR discontinue use of the product if mitigations are unavailable.
Known Detected Oct 18, 2023
https://www.netscaler.com/blog/news/cve-2023-4966-critical-security-update-now-available-for-netscaler-adc-and-netscaler-gateway/, https://support.citrix.com/article/CTX579459/netscaler-adc-and-netscaler-gateway-security-bulletin-for-cve20234966-and-cve20234967 ; https://nvd.nist.gov/vuln/detail/CVE-2023-4966
Affected Products
The following products are affected by CVE-2023-4966
vulnerability.
Even if cvefeed.io is aware of the exact versions of the
products
that
are
affected, the information is not represented in the table below.
CVSS Scores
| Score | Version | Severity | Vector | Exploitability Score | Impact Score | Source |
|---|---|---|---|---|---|---|
| CVSS 3.1 | CRITICAL | [email protected] | ||||
| CVSS 3.1 | HIGH | [email protected] |
Solution
- Upgrade to version 13.0-92.19, 13.1-49.15, 14.1-8.50 or later.
- Refer to vendor documentation for security updates.
Public PoC/Exploit Available at Github
CVE-2023-4966 has a 50 public
PoC/Exploit available at Github.
Go to the Public Exploits tab to see the list.
References to Advisories, Solutions, and Tools
Here, you will find a curated list of external links that provide in-depth
information, practical solutions, and valuable tools related to
CVE-2023-4966.
| URL | Resource |
|---|---|
| http://packetstormsecurity.com/files/175323/Citrix-Bleed-Session-Token-Leakage-Proof-Of-Concept.html | Third Party AdvisoryVDB Entry |
| https://support.citrix.com/article/CTX579459 | Vendor Advisory |
| http://packetstormsecurity.com/files/175323/Citrix-Bleed-Session-Token-Leakage-Proof-Of-Concept.html | Third Party AdvisoryVDB Entry |
| https://support.citrix.com/article/CTX579459 | Vendor Advisory |
| https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4966 | US Government Resource |
CWE - Common Weakness Enumeration
While CVE identifies
specific instances of vulnerabilities, CWE categorizes the common flaws or
weaknesses that can lead to vulnerabilities. CVE-2023-4966 is
associated with the following CWEs:
Common Attack Pattern Enumeration and Classification (CAPEC)
Common Attack Pattern Enumeration and Classification
(CAPEC)
stores attack patterns, which are descriptions of the common attributes and
approaches employed by adversaries to exploit the CVE-2023-4966
weaknesses.
We scan GitHub repositories to detect new proof-of-concept exploits. Following list is a collection of public exploits and proof-of-concepts, which have been published on GitHub (sorted by the most recently updated).
CVE-2025-5777
Python
Threat intelligence and incident response case study on LockBit ransomware exploiting CVE-2023-4966 (Citrix Bleed).
None
JavaScript TypeScript
MCP server for Qualys security APIs - 61 tools across 13 modules
Go Shell Python
CTT-Citrix-RCE: Temporal Resonance Citrix Exploit Score: 9.8/10 (Highest-rated exploit on platform) Description: "CTT-enhanced Citrix NetScaler RCE using 33-layer temporal resonance, α-dispersion payloads, and prime-aligned timing. Evades all signature and timing-based detection."
Python
Demo of a Kafka based anomaly detection system. Four public vulnerability feeds, stream processing. SBOM to CVE matching, factoring in EPSS, KEV, etc.
Python Shell PLpgSQL Dockerfile
Mari Exploit is a powerful automated exploitation framework designed for Red Teamers. It features a modular architecture, multi-threaded mass scanning, and auto-dorking capabilities, pre-loaded with high-impact exploits like XAMPP WebDAV, Laravel Ignition RCE, and more.
Python
AI-powered threat intelligence system combining malware behavioral analysis with LLM-generated cybersecurity recommendations for SharePoint and Citrix exploitation campaigns
Python
None
Python
None
Makefile HTML C++
None
None
None
Python Shell
CVE-2025-5777 (CitrixBleed 2) - Critical memory leak vulnerability affecting Citrix NetScaler ADC and Gateway devices
citrix cve-2025-5777 netscaler citrixbleed2
Python
Memory disclosure vulnerability in Citrix NetScaler ADC and Gateway when configured as a Gateway (VPN virtual server, ICA proxy, CVPN, RDP Proxy).
citrix citrix-netscaler cve-2025-5777
Python
Results are limited to the first 15 repositories due to potential performance issues.
The following list is the news that have been mention
CVE-2023-4966 vulnerability anywhere in the article.

-
The Cyber Express
INC Ransom’s Franchise Model Is Putting Critical Infrastructure on the Chopping Block
When Australia’s cyber watchdog issued a fresh advisory on INC Ransom, security teams worldwide are bound to take note — not because INC is new, but because the group’s business model has quietly made ... Read more

-
CybersecurityNews
Top 20 Most Exploited Vulnerabilities of 2025: A Comprehensive Analysis
The cybersecurity landscape of 2025 has been marked by an unprecedented surge in vulnerability exploitation, with threat actors leveraging critical flaws across enterprise software, cloud infrastructu ... Read more

-
The Cyber Express
Stolen VPN Credentials Most Common Ransomware Attack Vector
Compromised VPN credentials are the most common initial access vector for ransomware attacks, according to a new report. Nearly half of ransomware attacks in the third quarter abused compromised VPN c ... Read more

-
cybereason.com
Cybereason TTP Briefing Q3 2025: LOLBINs and CVE Exploits Dominate
Explore the latest trends, techniques, and procedures (TTPs) our incident response (IR) experts are actively facing with the TTP Briefing Q3 2025, a report built on frontline threat intelligence from ... Read more

-
The Register
Thousands of Citrix NetScaler boxes still sitting ducks despite patches
Thousands of Citrix NetScaler appliances remain exposed to a trio of security flaws that the vendor patched this week, one of which is already being actively exploited in the wild. Fresh data from the ... Read more

-
The Register
Major outage at Pennsylvania Attorney General's Office blamed on 'cyber incident'
The Pennsylvania's Office of Attorney General (OAG) is blaming a digital blackout of its services on a "cyber incident." The OAG posted a statement to Facebook yesterday, saying that its systems are c ... Read more
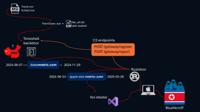
-
Daily CyberSecurity
ShadowSyndicate’s Global Ransomware Empire Blurs Lines Between Cybercrime and Geopolitical Espionage
Attack infrastructure of ShadowSyndicate overlaps with Toneshell, Rustdoor and Koi stealer | Image: Intrinsec In a recent investigation, cybersecurity firm Intrinsec has illuminated the sprawling infr ... Read more

-
The Hacker News
CISA Adds Citrix NetScaler CVE-2025-5777 to KEV Catalog as Active Exploits Target Enterprises
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting Citrix NetScaler ADC and Gateway to its Known Exploited Vulnerabilities (KEV) cata ... Read more

-
The Register
Now everybody but Citrix agrees that CitrixBleed 2 is under exploit
The US Cybersecurity and Infrastructure Security Agency has added its weighty name to the list of parties agreeing that CVE-2025-5777, dubbed CitrixBleed 2 by one researcher, has been under exploitati ... Read more

-
Cyber Security News
PoC Exploits for CitrixBleed2 Flaw Released – Attackers Can Exfiltrate 127 Bytes Per Request
Security researchers have released proof-of-concept exploits for a critical vulnerability dubbed “CitrixBleed2” affecting Citrix NetScaler ADC and Gateway products. The vulnerability, tracked as CVE-2 ... Read more

-
BleepingComputer
Public exploits released for CitrixBleed 2 NetScaler flaw, patch now
Researchers have released proof-of-concept (PoC) exploits for a critical Citrix NetScaler vulnerability, tracked as CVE-2025-5777 and dubbed CitrixBleed2, warning that the flaw is easily exploitable a ... Read more

-
Cyber Security News
“CitrixBleed 2” Vulnerability PoC Released – Warns of Potential Widespread Exploitation
Critical flaw in Citrix NetScaler devices echoes infamous 2023 security breach that crippled major organizations worldwide. The new critical vulnerability in Citrix NetScaler devices has security expe ... Read more

-
Help Net Security
CitrixBleed 2 might be actively exploited (CVE-2025-5777)
While Citrix has observed some instances where CVE-2025-6543 has been exploited on vulnerable NetScaler networking appliances, the company still says that they don’t have evidence of exploitation for ... Read more

-
Daily CyberSecurity
Citrix Bleed 2: ReliaQuest Warns of Active Exploitation in NetScaler Gateway Vulnerability
A newly discovered vulnerability—CVE-2025-5777, now dubbed Citrix Bleed 2—is raising serious security alarms. According to ReliaQuest, attackers are actively exploiting this vulnerability in the wild ... Read more

-
BleepingComputer
Citrix Bleed 2 flaw now believed to be exploited in attacks
A critical NetScaler ADC and Gateway vulnerability dubbed "Citrix Bleed 2" (CVE-2025-5777) is now likely exploited in attacks, according to cybersecurity firm ReliaQuest, seeing an increase in suspici ... Read more

-
The Register
Citrix bleeds again: This time a zero-day exploited - patch now
Hot on the heels of patching a critical bug in Citrix-owned Netscaler ADC and NetScaler Gateway that one security researcher dubbed "CitrixBleed 2," the embattled networking device vendor today issued ... Read more

-
BleepingComputer
New 'CitrixBleed 2' NetScaler flaw let hackers hijack sessions
A recent vulnerability in Citrix NetScaler ADC and Gateway is dubbed "CitrixBleed 2," after its similarity to an older exploited flaw that allowed unauthenticated attackers to hijack authentication se ... Read more

-
Cyber Security News
Citrix NetScaler ADC and Gateway Vulnerability Actively Exploited in the Wild
Cloud Software Group has issued an urgent security advisory warning customers about a critical memory overflow vulnerability in NetScaler ADC and Gateway products, which could enable denial-of-service ... Read more

-
The Hacker News
Citrix Bleed 2 Flaw Enables Token Theft; SAP GUI Flaws Risk Sensitive Data Exposure
Data Privacy / Vulnerability Cybersecurity researchers have detailed two now-patched security flaws in SAP Graphical User Interface (GUI) for Windows and Java that, if successfully exploited, could ha ... Read more

-
The Register
Don't panic, but it's only a matter of time before critical 'CitrixBleed 2' is under attack
Citrix patched a critical vulnerability in its NetScaler ADC and NetScaler Gateway products that is already being compared to the infamous CitrixBleed flaw exploited by ransomware gangs and other cybe ... Read more
The following table lists the changes that have been made to the
CVE-2023-4966 vulnerability over time.
Vulnerability history details can be useful for understanding the evolution of a vulnerability, and for identifying the most recent changes that may impact the vulnerability's severity, exploitability, or other characteristics.
-
Modified Analysis by [email protected]
Oct. 24, 2025
Action Type Old Value New Value Added Reference Type CISA-ADP: https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4966 Types: US Government Resource -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4966 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Removed Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4966 -
CVE Modified by 134c704f-9b21-4f2e-91b3-4a467353bcc0
Oct. 21, 2025
Action Type Old Value New Value Added Reference https://www.cisa.gov/known-exploited-vulnerabilities-catalog?field_cve=CVE-2023-4966 -
Modified Analysis by [email protected]
Mar. 13, 2025
Action Type Old Value New Value -
CVE Modified by [email protected]
Feb. 13, 2025
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. -
CVE Modified by [email protected]
Feb. 03, 2025
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. -
Modified Analysis by [email protected]
Jan. 27, 2025
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. -
CVE Modified by [email protected]
Nov. 21, 2024
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. -
CVE Modified by af854a3a-2127-422b-91ae-364da2661108
Nov. 21, 2024
Action Type Old Value New Value Added Reference http://packetstormsecurity.com/files/175323/Citrix-Bleed-Session-Token-Leakage-Proof-Of-Concept.html Added Reference https://support.citrix.com/article/CTX579459 -
Modified Analysis by [email protected]
Aug. 14, 2024
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. -
CVE Modified by [email protected]
Aug. 02, 2024
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. -
Modified Analysis by [email protected]
Jun. 17, 2024
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. -
CVE Modified by [email protected]
May. 14, 2024
Action Type Old Value New Value -
CVE Modified by [email protected]
Feb. 29, 2024
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. -
Modified Analysis by [email protected]
Jan. 09, 2024
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Changed Reference Type http://packetstormsecurity.com/files/175323/Citrix-Bleed-Session-Token-Leakage-Proof-Of-Concept.html No Types Assigned http://packetstormsecurity.com/files/175323/Citrix-Bleed-Session-Token-Leakage-Proof-Of-Concept.html Third Party Advisory, VDB Entry -
CVE Modified by [email protected]
Nov. 07, 2023
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server. -
CVE Modified by [email protected]
Oct. 25, 2023
Action Type Old Value New Value Changed Description Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA ?virtual?server. Added Reference http://packetstormsecurity.com/files/175323/Citrix-Bleed-Session-Token-Leakage-Proof-Of-Concept.html [No Types Assigned] -
Initial Analysis by [email protected]
Oct. 18, 2023
Action Type Old Value New Value Added CVSS V3.1 NIST AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N Changed Reference Type https://support.citrix.com/article/CTX579459 No Types Assigned https://support.citrix.com/article/CTX579459 Vendor Advisory Added CWE NIST NVD-CWE-noinfo Added CPE Configuration OR *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:fips:*:*:* versions from (including) 12.1 up to (excluding) 12.1-55.300 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:ndcpp:*:*:* versions from (including) 12.1 up to (excluding) 12.1-55.300 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:-:*:*:* versions from (including) 13.0 up to (excluding) 13.0-92.19 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:fips:*:*:* versions from (including) 13.1 up to (excluding) 13.1-37.164 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:-:*:*:* versions from (including) 13.1 up to (excluding) 13.1-49.15 *cpe:2.3:a:citrix:netscaler_application_delivery_controller:*:*:*:*:-:*:*:* versions from (including) 14.1 up to (excluding) 14.1-8.50 *cpe:2.3:a:citrix:netscaler_gateway:*:*:*:*:*:*:*:* versions from (including) 13.0 up to (excluding) 13.0-92.19 *cpe:2.3:a:citrix:netscaler_gateway:*:*:*:*:*:*:*:* versions from (including) 13.1 up to (excluding) 13.1-49.15 *cpe:2.3:a:citrix:netscaler_gateway:*:*:*:*:*:*:*:* versions from (including) 14.1 up to (excluding) 14.1-8.50
Vulnerability Scoring Details
Base CVSS Score: 9.4
Exploit Prediction
EPSS is a daily estimate of the probability of exploitation activity being observed over the next 30 days.
94.35 }} -0.00%
score
0.99954
percentile